
The Scammed IT Guy
“Grandpa, here is my presentation, could you please to share couple of minutes for me? And min mg mg started his presentation. Introduction: my name is Min Mg Mg, I’m studying on cyber security. I’m studying by “googling” and the main source of my studying is mostly Hacker High School www.hackerhighschoool.org. They are non-profit organization they help teens learn hacking as a method to figure out how things work. And for the people like us, can’t afford much to learn technologies can learn free lessons there. Now there will be available video trainings soon and they are even starting HHS academy. Let me mention the moto of them and there definition for hacking in short; these are; “Hack everything but harm none” and “Hacking is a method of problem-solving and learning”. And very soon, I’m going to study at the new org that’s building by the HHS’s project manager, called (S4H) www.schoolforhackers.org where also available video trainings as well. Subject: The topic I want to mention is – a greedy IT guy ends up having less , who scammed a company –relied him for the technology issues. Let’s get hands dirty The investigator was good but his eyeballs out amazingly to hear the price from someone’s saying and “what, for point to point wireless installation was costed about US$ 3000?” he asked and “what’s the distance, what are the devices they used and is there some blocked building within the points?” he went ahead. “The distance is 5.6 km by car, yet it is only about 4 km directly to connect and able to see each other, I don’t know the devices used exactly” someone answered. And the investigator decided to get his hands dirty for the reason of his previous company. And had an immediate call to the secretary of the abc company. She’s already a friend, yet she’s not trustworthy in this circumstance, he used a method of social engineering. Conversations –“Investigator: Hello, Ms. Secretary, it has been so long. And is everyone good? Secretary: Of course, everyone is doing well. And you and what are u doing there? Investigator: So am I, and now I’m getting busy to find some providers to scribe point to point wireless connection but the lines are busy and I’ve done nothing yet. And my boss is so being rush to get these. I’ve heard that at your company the wireless connection has been installed recently. If so, I hope you might want to help me up some information on this? So that I can reach my boss with the report back, do you mind, please? Secretary: Of course, I could give you a hand but I can’t name what are these I’ll send you an email of a copy of the price list what our IT Manager applied for approval. Investigator: Oh thank goodness! Very soon after the conversation, the price list and the devices information were sent from secretary@abc.com, and then he opened with his heart beats. “Umm, all of these devices are for point to point connection? And the letter head seem a bit nebulous. Y Company Att: IT Manager (abc company) Subject: point to point wireless installation cost
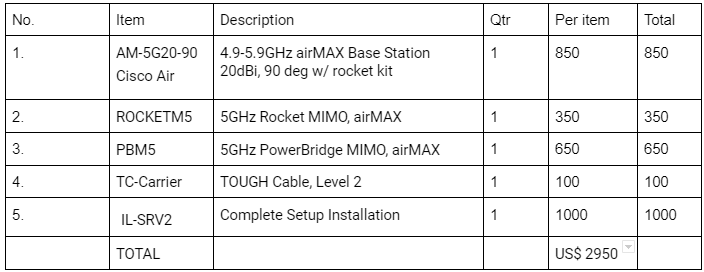
“apprantely, the letter seems surely nebulous like reprint out after modified the contents. And, the number one AM-5G20-90 at the top of the list is surely Ubiquiti model but what the Cisco Air actually is? And why this amount TC-Carrier has to be used? That’s so interesting.” And he decided to call the supplier company and try to know something real. Investigation – but then, social engineering; Investigator: Hello, is it from Y Company? Y Company: Yes, May I help you? Investigator: I’m the consultant at the IT section of the company abc. Recently our company has purchased a wireless service of your company. Now, I’ve an issue to ask a favor, if you don’t mind I would like you to send mail the copy of the receipt for the point to point service we purchased recently to our management’s mail that I’ve to apply it at our budget meeting with director. I just asked the favor because our IT Manager is travelling and we couldn’t contact him yet. Would that be ok? Y Company: we’ll contact you back after the confirmation with our sale manager, sir. Investigator: if I may, I’ll hang on the line because all including our director is waiting in the meeting room and I’m getting at the dead end. Or, just tell me the total amount of the cost, please? Y Company: Hang on a moment, I’ll inform him and put you through. Sale Manager at Y Company: We’ll be doing the favor for you, sir. The total amount of the cost was US$ 1601. But I’ll only send the softcopy of it to the address of your management’s email. Investigator: You are so kind, our management’s email address is secretary@abc.com and it goes directly to director office. While investigator was sitting at his computer with a cup of coffee, the secretary of abc company gave a ring. And “I just dialed you because now I just have received an email from the Y Company. They sent to us despite the subject says your name as mr. investigator’s request.” She said. “Yes, I asked them to send to the secretary of abc company and that’s the real receipt of the real cost from Y Company so that you could make sure the price list.” Investigator said. The real weakness of the Mr. Scammer was; he did the deception to the ones who’re less technological knowledge than him, unless he’s skillful. So, let’s take a look at the real price list of the Y Company; Y Company Att: IT Manager (abc company) Subject: point to point wireless installation cost
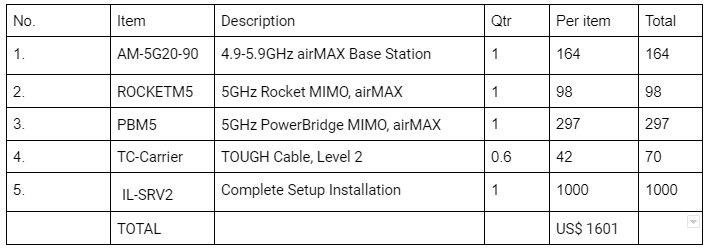
We all have been being scammed where we don’t understand both with and without our knowledge. But if there will be someone who can help us, frequently we think. Sometime, even the very one who is trustworthy to us might scam us. ”, let’s assume ourselves as the closest enemy of our own according to the one of the speeches of General Aung San; “get rid of the closest enemy, the first question we should ask ourselves is “Is it possible?” And firstly we have better get rid of credulousness. And think about insider. In this case, even if he’s a company’s IT staff why he was too bold to scam that amount? Does our management team need to be educated at technology related issues, or some of them were the partner of the Mr. Scammer?
A company that’s going with a lot of stuffs is like a house with many windows and entrances. Making sure to be sucure only a window or door never means the whole house is secure.
That’s why we surely need to have an ethical hacker and tight computer and network security policies.
“Engineering a social called Social Engineering is another term of lie?” Grandpa asked.
“Social Engineering can be known as psychological manipulating in shortly, a legitimate lie, but yelling ‘Fire!’ in a crowed movie-theater and in a public is unlawful. And some detail meaning of social engineering is….”